What is TinyCa
TynyCa is a great tool to create and manage ssl CAs, certificates and keys, without messing into the technical details of openssl.
It was very easy for me to create a self-signed certificate for my personal website following this tutorial, which also explains how to install in the server (apache) and in the client (firefox) all the required files.
The problem of multiple domains and subdomains
In the linked tutorial, at some point (in the request creation dialog) you have to fill in the “Common Name” for the certificate. This identifies the host for which the certificate will be used.
For instance, for my website pietrobattiston.it, I would just put pietrobattiston.it in this field.
What's the problem? That I may want to use the same certificate for more than one website.
You may think that's generally not particularly smart, since (self-signed) certificates are cheap… but in my case, I wanted my website (the same website!) to be accessed at both https://pietrobattiston.it and https://www.pietrobattiston.it, and it seemed stupid to create two different certificates just to address the possible absence of the “www” prefix. But more in general, it can make sense to use the same certificate for multiple third-level domains.
The solution is provided by OpenSSL with the Subject Alternative Name (or subjectAltName) field in the certificate.
The solution
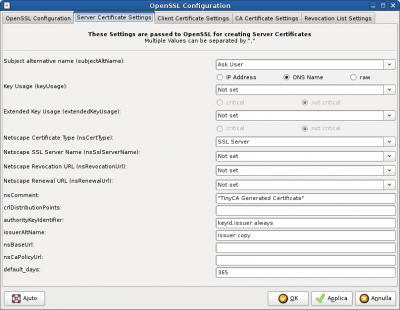
TinyCA (all this page refers to version 0.7.5) can manage this field, but it is not shown by default, since it is considered “expert mode”. To enable it, click on Preferences → OpenSSL Configuration (yes, just below Experts Only!…) A window will open: click on the Server Certificate Settings tab.
Under “Subject alternative name (subjAltName)”, select “Ask User”, and just below select “DNS Name”.
Click “Apply” and then “OK” to go back to the main window. Now, assuming that you already created your request as described in the tutorial, right-click on it and select “Sign Request” and then “Sign Request (server).1)
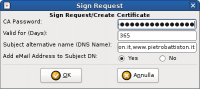
In the small dialog that pops up, there is now a field labeled ”Subject alternative name (DNS Name):“: you must write inside it a comma-separated list of all desired hostnames, including the one you already inserted as “Common Name” of the request:2)
So in my case this field had the following value:
pietrobattiston.it,www.pietrobattiston.it
Now enter your CA password, click OK and that's all: you can now proceed to the installation of the certificate, as the tutorial describes.